
In the last three years, one in two companies have experienced a successful cybersecurity attack (SoSafe Awareness). With figures this high, it can be hard to understand what the root cause is. “Cyber Attack” is a very broad term that covers a wide range of different exploits, and will often constitute a multi-step approach that can be classed as different attacks. One of the most important steps in a successful attack, and ultimately one of the most important things to be aware of as a professional, is phishing attacks; it was recorded by Spanning that 90% of attacks will begin their initial probing phase as a phishing attack.
What Is Phishing
Phishing attacks can vary in complexity, but at their roots, phishing attacks are conducted by sending you a malicious email. This email either contains a payload that will download onto your computer, directs you to a malicious website that allows a threat actor to access your computer, or directs you to a fake login screen to record your details.
How To Spot Phishing Emails
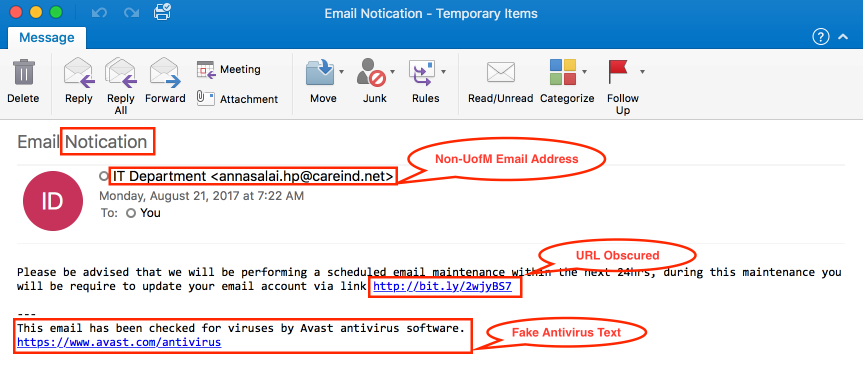
There are multiple ways to spot phishing emails. The easiest way to spot them is to check the email header. The email header will include who has sent the email, the address it is from, and the domain name. If the email is saying it is from Santander, an “@Paynow” domain would be suspicious, even if the whole email is “Santander@Paynow”; a bank isn’t going to have its domain as “Paynow”.
Another common way of verifying if the email is suspicious is checking the grammar of the email. Emails from companies will almost always be checked for spelling and grammar before they are sent, whereas spam emails will not. This is a good way to verify the validity of an email, but it is not foolproof; an email asking you for money in a grammatically correct manner does not mean the email is not malicious.
An important note to make is how attackers are able to bypass the security measures in the email gateway. Most Email gateways will have a set of rules that will filter out certain emails if the text within them follows a certain pattern known to be malicious. This could include sentences asking for money, warning you of intruders in your social media, or claiming that you have won something. However, images are now being used to hide malicious emails from the Email gateways, because the gateways are unable to read the images. This allows attackers to make images that claim you have won something, but are actually links to malicious sites.
Phishing emails constitute a significant threat; AAG IT Services estimates that 3.4 billion spam emails are sent everyday, but their increasing sophistication means that Google is only able to block 100 million of them.
How To Stay Safe
To combat this ever-growing threat, there are many ways in which we can protect ourselves. To start, you should never click on any links from emails which request you to log into your accounts. That is not to say you should ignore the email entirely, but you should always avoid clicking on the links. Let’s say you have been asked to log into your gmail account: instead of clicking the link in the email, simply log in to your account directly through google. If there are any issues, you will see them once you have logged in, but you have eliminated the risk of clicking on the email.
There are many more examples of how to best protect yourself, but the difficulty is that the varieties of phishing attempts are always growing. Accordingly, the best course of action is to utilise training platforms which help companies strengthen their defences against phishing attacks. For example, the Mondas anti-phishing service provides regular training and simulation exercises for entire companies, as well as investigation and remediation in the event of a breach.
Conclusion
Ultimately if you are ever suspicious of an email, don’t click on it. No one will ever reprimand you for being cautious, especially in corporate environments where failing to spot a phishing email can carry high financial consequences. However, if you do fall victim to an attack, then notify someone immediately; a quicker response will always result in reduced damages for yourself and the company.
Want to see how you and your employees fare against phishing attacks? Click here to try our free phishing test, and contact us to find out how we can help.





