
Speak to an Expert
Speak to our CREST accredited experts, for a free quote around our comprehensive penetration testing services.

Scroll
Let our security experts discover your security weaknesses before they do.

Don’t wait for an attack to test your security controls, Mondas provides on demand, proactive security testing that allows you to ensure that your cyber defences are acting as expected. Real world simulated attacks that emulate true threat actors.
Mondas are a provider of penetration testing services. Our range of penetration testing engagements help organisations to effectively manage cyber security risk by identifying, safely exploiting, and helping to remediate vulnerabilities that could otherwise lead to data and assets being compromised by malicious attackers.

Penetration testing, often known as pen testing or ethical hacking is a simulated cyber attack where an attempt is made to evaluate the security of an IT infrastructure by safely trying to exploit potential vulnerabilities.

Speak to our CREST accredited experts, for a free quote around our comprehensive penetration testing services.


A firewall monitors the incoming and outgoing traffic of your network, and works to filter out and detect various forms of malware, phishing, and other forms of cyber attacks. Our external penetration testing will help detect any gaps or weaknesses in your current firewall setup.


Your internal network has a variety of potential points of attack for hackers, from systems and hosts to various networking devices. Mondas’ network penetration test consulting services help you discover which parts of your network are most vulnerable.


Whether you work with Amazon Web Services (AWS), Microsoft Azure, or any other cloud service provider large or small, we’ll help you conduct quick and effective cloud computing penetration testing to ensure the safety and security of data handled by any cloud vendors or partners.


Mondas can conduct web application pen testing via either a Whitebox or Blackbox approach, in conjunction with manual inspection and reviews. We’ll guide you through the entire process, from information gathering and identity management testing to cryptography and client-side testing.


Today’s hackers aren’t just limiting themselves to phishing and malware. Physical servers, personal computers, and company-issued laptops are all vulnerable hardware entry points. Use Mondas’ hardware penetration testing services to secure all your organization’s physical endpoints.


Mobile and smartphone devices have become indispensable for most businesses today. Whether it’s an iPhone, Android, or any other connected device, work with Mondas to conduct mobile external penetration testing to secure all organisational data handled on smartphones.


Mondas offers a variety of penetration testing services that aid businesses in gaining compliance with relevant agencies and regulatory bodies. This includes PCI-DSS, HIPAA, and NIST penetration testing that helps prevent any fines or penalties that may result from non-compliance.

Speak to our CREST accredited experts, for a free quote around our comprehensive penetration testing services.

Red teaming is the practice of rigorously challenging plans, policies, systems and assumptions by adopting an oppositional approach.


A simulated cyber-attack is as close as you can get to understanding how prepared your organisation is to defend against a highly skilled and persistent hacker.
The main differences between red teaming and penetration testing are depth and scope. Pen testing is designed to identify and exploit as many vulnerabilities as possible over a short period of time, while red teaming is a deeper assessment conducted over a period of weeks and designed to test an organisation’s detection and response capabilities and achieve set objectives.
A Red Team Operation from Mondas will exceed the remit of traditional security testing by rigorously challenging the effectiveness of technology, personnel and processes to detect and respond to a highly targeted attack conducted over an extended period of time.
Take a look through our free brochure to understand how Mondas can help you reach your Cyber Security goals.

Red teaming uncovers risks to your organisation that traditional penetration tests miss because they focus only on one aspect of security or an otherwise narrow scope.
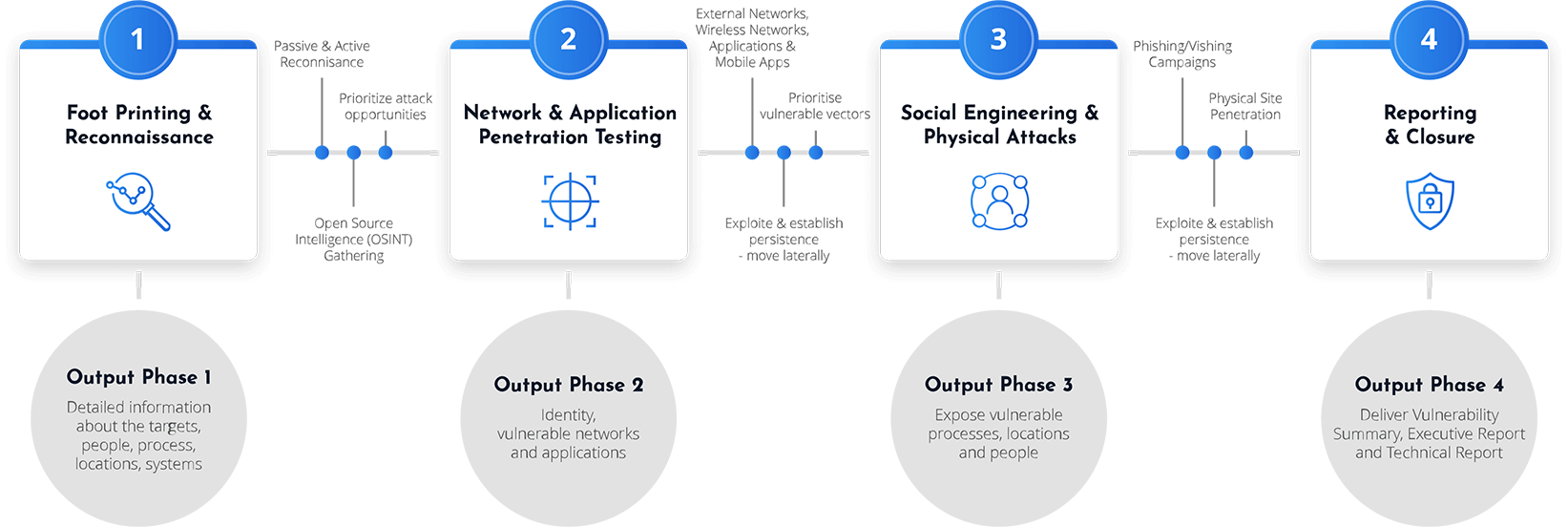
Tap to enlarge

A red teaming engagement is performed from as close to a zero knowledge perspective as possible, meaning your organisation as a whole is not notified ahead of time, nor is the red team supplied with any pre-requisite information up-front, to closely mirror a real time attack.


Learn how prepared your organisation is to respond to a targeted attack designed to test the effectiveness of people and technology.


Learn whether systems, data and other critical assets are at risk and how easily they could be targeted by threat actors.


Red teaming can help identify hidden vulnerabilities that attackers might seek to exploit.


Receive important post-operation support to address any vulnerabilities identified and mitigate the risk of suffering real-life attacks.


By simulating a range of scenarios, red team testing helps your security team to identify and address gaps in threat coverage and visibility.


Better understand your organisation’s security weaknesses and ensure that future investments deliver the greatest benefit.

Speak to our CREST accredited experts, for a free quote around our comprehensive penetration testing services.
When completing a Red Team Exercise we will set out specific goals in order to gain a better understanding of the vulnerabilities within your organisation which may be exploited during an attack.



