
The world of cybersecurity is changing rapidly, the types of threats and attack vectors are diversifying and changing continuously. The attacks have migrated to increasingly sophisticated APTs, insider attacks, fraud, and cybercrime. Traditional security solutions are not enough to face this new landscape of security challenges, and organisations and users need to be at the forefront of the latest technologies in use.
Cybersecurity is an area in which high-performance, real-time analysis such as that provided by Big Data is essential, as attacks are being carried out in less time and new threats emerge in a matter of seconds. In this area, there are a multitude of data sources to feed Big Data, such as logs of all kinds of systems (authentication, SIEM, IDS / IPS, etc.) and network devices, application logs (transaction log, authentications, interactions, etc.), social media data, message content, etc.
In this context, it is necessary to change the traditional passive approach, in which the necessary measures are taken once the cyberattack has been suffered, to a proactive stance. This new approach offers a point of view that includes advanced threat detection, real-time identification of risks, as well as the application of protection measures and countermeasures.
Big Data, in combination with predictive analytic techniques, allow the identification of behavioural patterns and trends, which gives the ability to anticipate a multitude of cyber-attacks, which are characterised by being relatively random, spontaneous and out of the ordinary.
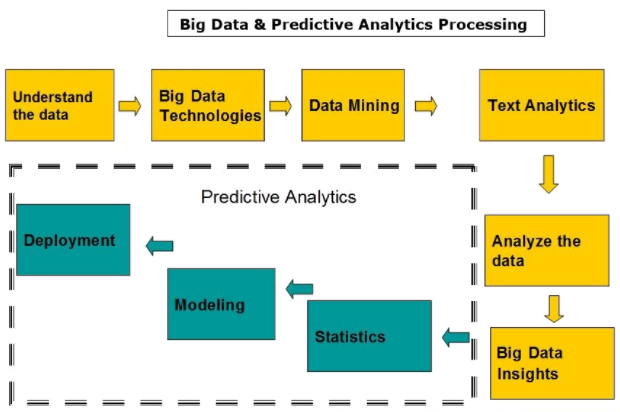
To move to a proactive approach with the use of real-time analytics, typical of predictive environments, a series of measures must be taken:
- Map and leverage existing data sources: organisations have a large amount of existing or easily accessible data that could help improve security. Data sources range from information on the network to web activity logs, through Netflow information, server logs, etc. Once the data has been mapped, its value needs to be evaluated in further analysis.
- Contextualise and connect data: when an organisation understands the information it handles, the next step is to establish its context, and then relate it to other data, network information, and architecture components. This builds the
active threat and risk models for the organisation and these models can be analysed with predictive machine learning techniques.
- Using deep analytics to refine these models: understanding the context of the data and then connecting its pieces is just the beginning. The use of new analytical capabilities refines the model, providing useful metrics, adequate information and recommendations for making decisions about current and future risks.
Taking these data into account, the main advantages of using predictive analysis techniques in data processing and cybersecurity can be grouped into three sections:
- Prevention counts for two: cybersecurity requires an increasingly proactive approach. You need to be able to crunch the data, identify patterns, and detect anomalies in near real time so that you can take action before the data is stolen. Predictive analytics not only identifies where cybercriminals have tried to attack in the past, but helps to see where they are likely to attack next, where their weak spots are, and how prepared an organisation (or a particular system) is to counter an attack before it’s too late.
- Handling large volumes of data: one of the biggest challenges for a robust cybersecurity solution is dealing with huge pools of data, which can be very difficult to sift through, process, and analyse for useful information. These data streams can come from a wide range of programs, databases, and devices, which means that a powerful tool is needed to keep them all in sync. However, once you have a system capable of performing this task, the more input variables you have to analyse, the more complete the image you will get and the more accurate your predictions will be.
- Automation of much of the workload: predictive analytics techniques and machine learning can help extract information data and draw crucial conclusions very quickly, while eliminating part of the workload for the IT department. Of course, an expert will still be needed to accurately interpret the findings and patterns, but much of the hard work of collecting, collating, and compiling reports is done automatically. This means that the IT team can focus on identifying potential threats and acting quickly to protect the system, rather than getting bogged down in daily
tasks.
Do you want to know more about how big data analytics can help with your cyber security strategy? Get in contact with our experts.





